If your GitHub forked master branch is ahead from the upstream's master branch and you wanted to make it even (i.e. also lose some work). The following procedure might help you.
Note: If you have your default branch protected perform steps 1, 2, 3, 7, 8 and 9. Otherwise just do steps 4, 5 and 6.
- Open a terminal (i.e. powershell, cmd, bash) and checkout the master of the upstream to a temporary branch (i.e. this could be anything) using the following syntax:
git checkout -b <temporary-branch> upstream/master
Example
git checkout -b temp-branch upstream/master
Where <temporary-branch> is temp-branch.
- Push the temporary-branch to your origin using the following syntax:
git push origin <temporary-branch>
Example
git push origin temp-branch
Using the <temporary-branch> from the example in step 1.
- On your browser, access your forked GitHub project and update the default branch to your temporary-branch.
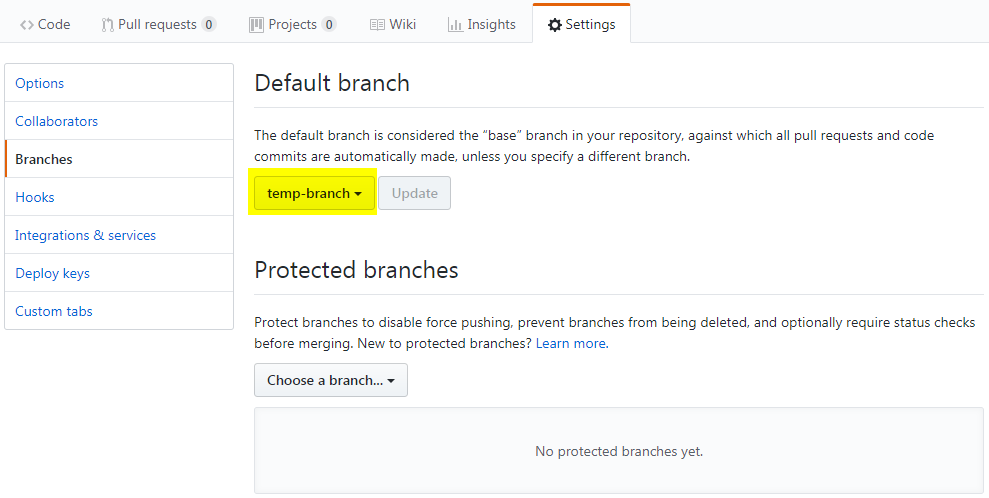
- On your terminal (i.e. powershell, cmd, bash), switch to your master branch using the following command:
git checkout master
- Reset the master based on the upstream's master branch using the following command:
git reset --hard upstream/master
- Push the update to your master using the following command:
git push origin master --force
Note: If you didn't do step 3 this and the branch is proctected command will fail.
- On your browser, access your forked GitHub project and update the default branch to master.
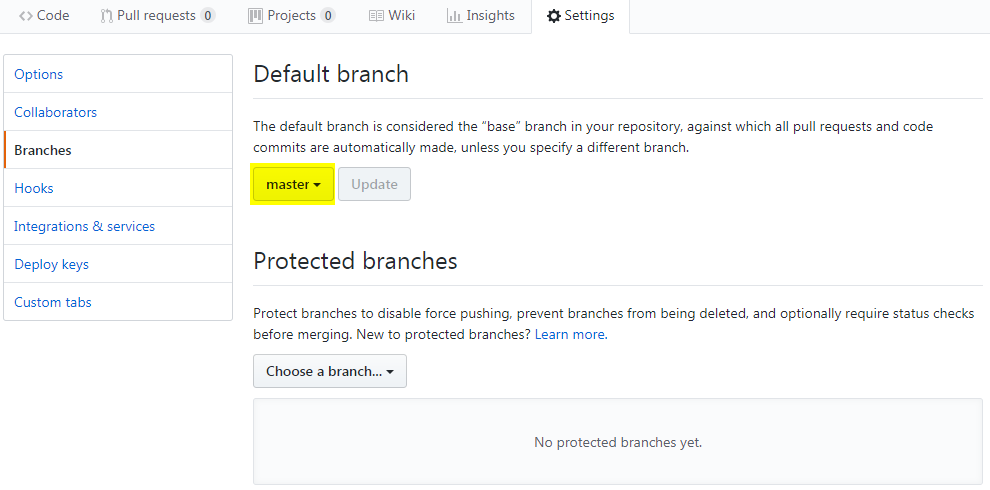
- Going back to your terminal, delete the local temporary-branch using the following syntax:
git branch -D <temporary-branch>
Example
git branch -D temp-branch
Using the <temporary-branch> from the example in step 1.
- Delete the remote temporary-branch on your origin using the following syntax:
git push origin --delete <temporary-branch>
Example
git push origin --delete temp-branch
Using the <temporary-branch> from the example in step 1.
Recent Comments